Recently, a hacker known as PeteRepete leaked over 533 million Facebook users’ personal information online. There were no passwords in the database, but it did contain full names, phone numbers, email addresses, employer information, and a few other pieces of information from Facebook users’ profiles. GroupSense confirmed only a small portion of the records contained email addresses, but almost all of the records contained a phone number.
Many news outlets mentioned threat actors can use mobile numbers to perform something known as a SIM swap. SIM swapping, also known as SIM jacking or porting, is a technique used by cybercriminals to steal victims’ phone numbers.1 A successful SIM swap enables a threat actor to intercept phone calls and text messages and exploit the login and multi-factor authentication procedures of websites such as Venmo and PayPal.
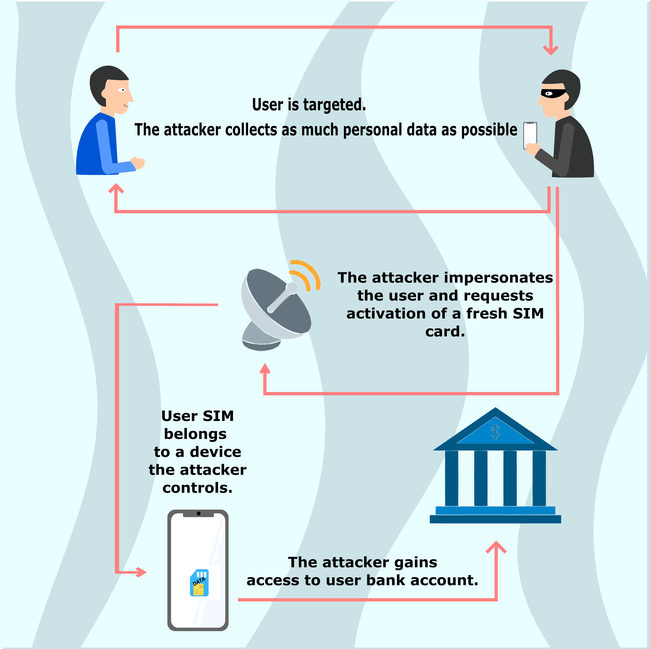
SIM swapping is surprisingly not that difficult. Depending on your phone carrier, when you get a new phone you typically have to call a number and provide some identifying information to authenticate your identity before the carrier activates your SIM. A threat actor can do the same thing, with the only difference being they impersonate their victims and convince the cell phone carriers to activate a SIM within a phone they have in their possession. To do this, the threat actor needs to perform some reconnaissance to gather victim identity information; they will often use open source research, social engineering, or phishing attacks to gather the information.1
Once a threat actor has access to a victim’s phone number, they can target the victim’s accounts using weak multi-factor authentication. Since many services allow password resets with only access to a recovery phone number, a threat actor is able to gain access to almost any account tied to the victim’s phone number. As a result, threat actors could potentially directly transfer funds from a bank account or cryptocurrency wallet, extort the rightful owner, or sell accounts on the dark web.
Figure 1: An example of how a SIM swap attack could take place; Source: Privacy Pros
Celebrity SIM Swaps
In early February 2021, the UK’s National Crime Agency (NCA) arrested eight people in connection to a series of SIM swapping attacks targeting US celebrities. The arrests took place in England and Scotland as part of an ongoing investigation which included the US Secret Service, Europol and other international agencies. The threat actors involved used social engineering on US cell phone providers to assign celebrities’ phone numbers on a SIM card the threat actors had in their possession.
Once they gained access to each victim’s phone number, they were able to access accounts and reset passwords while bypassing multi-factor authentication.
Europol said the gang stole more than $100 million worth of cryptocurrency using these methodologies.2
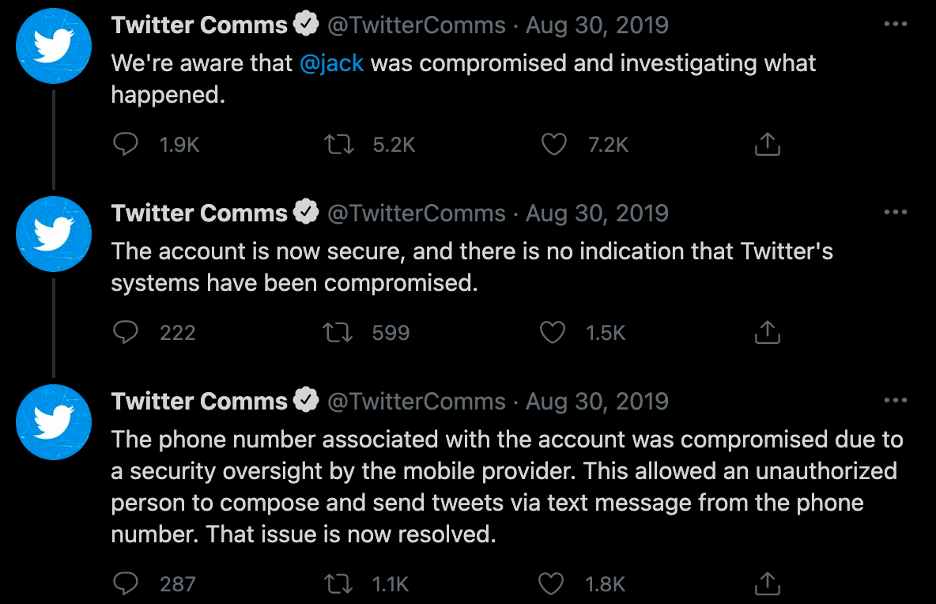
SIM Swappers Hijack Twitter of CEO Jack Dorsey
On 30 August 2019, threat actors known as The Chuckle Squad successfully hijacked the account of Twitter’s top executive Jack Dorsey through a SIM swap. The Chuckle Squad posted several offensive tweets from the executive’s Twitter, including racial slurs and anti-Semitic content.3 The offensive tweets were up for about 10 minutes before Twitter stepped in and removed them.
Low Barriers to Entry
For threat actors there are low barriers to entry to carry out their attacks due to a handful of key factors:
- Hijacking a SIM does not require a high level of technical expertise. Anyone with a mobile phone and internet access could potentially carry out a successful attack.
- A SIM swap attack does not take a lot of time to carry out. The most time-consuming part of a SIM swap attack is the reconnaissance on the intended victim. However, if a victim’s personal information is leaked in a data breach, the amount of time spent on research decreases significantly.
- Mobile phones, as well as SIM cards, are easy to obtain.
- Unfortunately, people lose or break their mobile phones all the time, which leads them to call their mobile providers to activate a SIM for a new phone. It’s common for cell phone providers to receive calls from their customers to change or activate a new SIM.
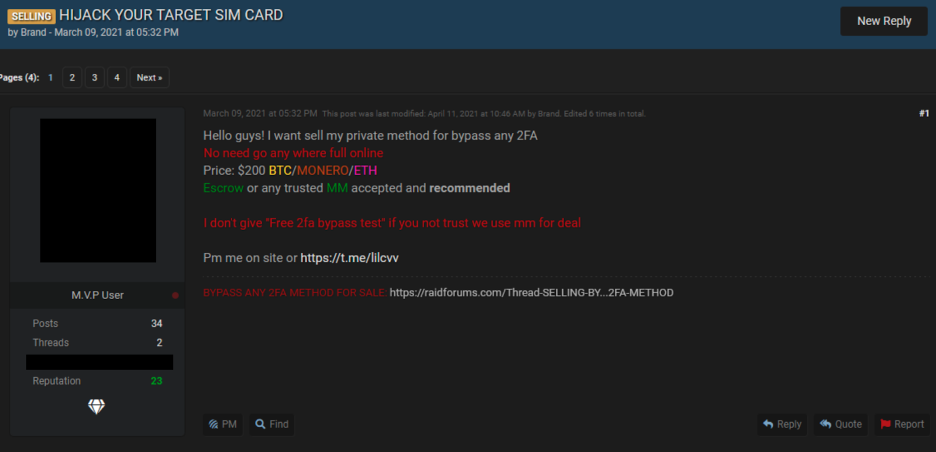
- The wide availability of SIM swapping services for sale on the deep and dark web can make the process easier. There are also methodologies and fraud guides available for purchase on hacking forums which allow low-level cybercriminals to get started.
Figure 3: A threat on a popular hacking forum offering SIM swapping services; Source: RaidForums
In the end, it is about awareness and training on both sides of the activation call to help authenticate the identity of callers. Princeton academics carried out a study testing five major cell phone providers to see if they could socially engineer call center employees into swapping a victim’s phone number onto a new SIM without providing the proper credentials. According to their report, “AT&T, T-Mobile, Tracfone, US Mobile, and Verizon Wireless were found to be using vulnerable procedures with their customer support centers, procedures that attackers could use to conduct SIM swapping attacks.”4
Potentially High Risk
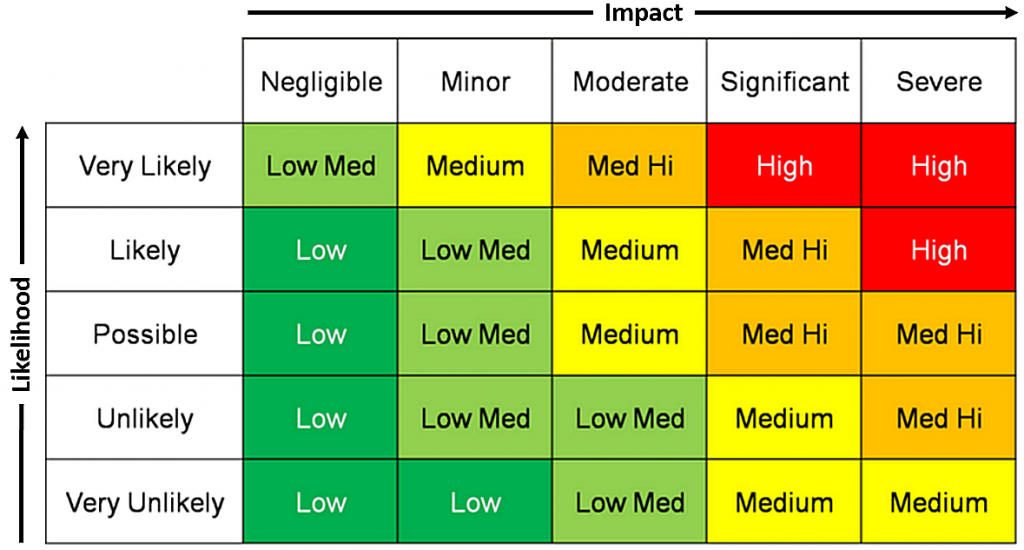
In order to intelligently measure the risk of a SIM swap attack, you have to determine the likelihood of exploitation as well as the potential impact. In the event that a threat actor targets you, what is the likelihood the attack would be successful? To start, you need to identify what security controls are in place to stop a threat actor in their tracks, such as a PIN or passphrase on your account with your cell phone provider.
A SIM swap attack could potentially be a high-impact attack because it can result in:
- Significant financial loss
- Cryptocurrency theft
- Loss of personal information
- Damage to reputation
- Account takeovers
Prevention Tips
Having the proper security controls in place will lower the likelihood of exploitation thus reducing the overall risk. Here are some prevention tips:
- Set up a PIN or passphrase on your account with your cell phone carrier to help prevent unauthorized changes to your account. Another proactive step would be to set up a passphrase or PIN with your financial institutions while you’re in the process of updating your account security features.
- Level Up: Don’t use the same passphrase or PIN with every vendor you deal with. Use a password manager like LastPass or Dashlane to securely store your passphrases and PINs.
- Require in-store assistance on your account with your cell phone carrier. It can be inconvenient having to go into the store, but needing to provide proper identification in-store could prevent successful SIM swap attacks.
- Use an authenticator application instead of a mobile phone SMS message for two-factor authentication whenever possible.
- Don’t respond to any suspicious text, voice, or email messages.
- Don’t overshare personal information on social media and other public platforms.
These are basic security tips you can take to better protect your accounts. You can also reach out to the organizations you receive services from to learn other ways you can secure your accounts. It will benefit you in the long run to have the proper security measures in place.
References
1https://attack.mitre.org/techniques/T1451/
2https://www.zdnet.com/article/authorities-arrest-sim-swapping-gang-that-targeted-celebrities/